December 16, 2024
Top eSIM Security Risks and How to Safeguard Your Customers From Them
While eSIMs improve mobile security compared to physical SIMs, they face new digital threats. Discover how providers and resellers can mitigate these risks and protect users.
It’s an interesting irony that though security is one of the appeals of eSIM cards over physical SIMs, it is also one impediment preventing its widespread adoption.
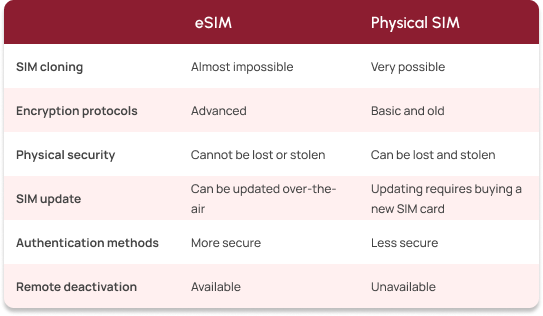
On the one hand, their superior authentication methods, advanced encryption protocols, and the fact that they can’t be physically lost or stolen make them safer than physical SIM cards.
On the other hand, hackers are now developing different innovative ways to access them remotely, raising concerns about their security.
However, these eSIM security risks are not intractable. As an eSIM reseller, you can improve eSIM security by:
- Putting in place strong security measures on your website or app
- Educating your customers about useful security tips
- Working with eSIM platforms with secure APIs and reputable carriers
By doing this, you can protect your customers and help them enjoy the improved mobile connectivity that eSIM provides without any risk to their data and money.
In this article, we will highlight the major eSIM security risks and identify the security protocols that eSIM providers can implement to safeguard their customers. We’ll cover:
- eSIM security: The security advantages of eSIM over physical SIM
- Are eSIMs secure? Top eSIM security risks
- Securing your customers: How eSIM providers can mitigate security risks
Do you want to securely resell eSIM connectivity services to your customers? Book a demo with zendit to learn how you can resell eSIMS by integrating your plug-and-play API into your website or app.
1. eSIM security: Advantages of eSIMs over physical SIMs
Before considering eSIM security risks, it is important to make it clear that they are superior to physical SIM cards when it comes to security concerns.
This will help us make the point later on that instead of ditching eSIMs, all relevant stakeholders should be working together to improve the security of eSIM technology.
So, how secure are eSIMs in comparison to traditional SIM cards?
eSIMs cannot be physically lost or stolen
Since eSIMs are embedded in the device, they cannot be removed. Thus, scammers cannot have physical access to the SIM. This absence of physical access makes certain scams difficult.
“Unlike SIM cards, eSIMs are not physically swappable and thus not exported to SIM swap attacks and identity theft,“ according to The Yale Wave, a blog operated on the Yale University website.
When a scammer steals a removable SIM card, they can put it in another device and use it to get all the authentication codes they need to access a user’s bank accounts and other sensitive information.
eSIMs can be updated over the air
eSIM users can receive security updates over-the-air (OTA). With these updates, certain vulnerabilities can be patched, making it more difficult for scammers to find their way through them.
Physical SIM cards cannot be updated in this way. The only way to “update” them is to get another.
eSIMs use more secure authentication methods
While physical SIM activation relies mostly on PINs that are sent to the device, eSIMs often use multi-factor authentication, including biometric verification and device-level authentication.
eSIMs can be remotely deactivated
When users suspect foul play, they can remotely deactivate an eSIM profile to prevent cyber attacks.
Disabling a physical SIM is harder. It often requires that the user contact the carrier, which will usually take more time.
eSIMs are harder to clone
Because eSIMs rely on device-bound cryptographic keys, they are more difficult to clone. On the other hand, physical SIMs can be easily cloned once the encryption is compromised.
“Mobile network operators tightly control the setup and management of eSIM profiles, making it nearly impossible for hackers to clone them,” according to Aurelija Skebaitė, a copywriter at NordVPN, a cybersecurity company.
eSIMs use advanced encryption
Encryption is the technology that encodes information exchanged between two parties, ensuring that a third party does not gain access to it.
eSIMs come with advanced encryption protocols and secure elements that ensure secure data transmission and the protection of sensitive data.
“The communication between the device and the carrier’s servers is encrypted, which means that the activation process cannot be intercepted,” according to Srdjan Gombar, a content manager, writing for Cyber Management Alliance, a cybersecurity consulting firm. “The level of encryption is pretty high, which ensures that there’s an incredibly low chance that something bad will happen.”
eSIMs also make it easier to trace the activities of scammers.
“Even if something unsanctioned is to happen, you need to keep in mind audit trails and monitoring,” he continued. “In other words, you can track all the eSIM activity, including when the profile-switching was made, who made it, etc.”
eSIMs have security standards enforced by regulatory bodies
A regulatory body like the Groupe Speciale Mobile Association (GSMA) issues stringent security standards that device manufacturers and mobile network operators must comply with. These standards include cryptographic measures, remote provisioning processes, and encryption protocols.
2. Are eSIMs secure? Top eSIM security risks
Despite the security advantages of eSIMs, certain eSIM security concerns remain.
In response to the question, “Can an eSIM be hacked?” Skebaite answered: “eSIM (embedded subscriber identity module) technology employs various additional security measures that make it less prone to hacking than physical SIMs.”
Nevertheless, she had to acknowledge that eSIMs can still be hacked.
“However, you should remember that no connected device is 100% immune to hacking,” she acknowledged. “And since eSIMs are used on connected devices, like any other technology, they are vulnerable to malware, social engineering, and phishing attacks.”

Let’s review some of these eSIM security risks:
Phishing or social engineering attacks
Social engineering attacks occur when hackers impersonate mobile network operators and pretend to help users with the activation of their eSIM profiles. They can establish a communication line via phone calls, SMS messages, social media messages, or emails.
They will request QR codes or authentication codes during this process and end up using them to create the eSIM profile on a device they control. With that, they can gain access to the user’s sensitive information.
Another strategy is to convince users that their eSIM profiles will be deactivated if they don’t send certain information or do certain things. They steal sensitive information in the process or even receive payments from users.
Malware attacks
Clicking on suspicious links, downloading apps from untrusted sources, and refusing to update the device’s operating system or eSIM security patches can expose users to malware attacks.
Malware attacks seek to install malware software on the device. With this software, hackers can steal sensitive information, monitor users’ activities, and even remotely control the device.
eSIM swap scams
Are eSIMs subject to SIM swap attacks?
The simple answer is yes.
These scams can occur in two ways.
First, scammers can impersonate end users and request that the mobile carrier switch them from a physical SIM to an eSIM. They will use the information of the user obtained through data breaches.
The new eSIM profile would be created on a device they control which will end up giving them control of the user’s phone number.
Second, scammers can request that the mobile network operator switch an eSIM profile from one device to another. Since they have the relevant information, they can convince the mobile carrier to do this without raising suspicion.
“SIM card swapping is a form of identity theft and fraud and is just as risky with eSIMs as with physical SIMs,” according to Skebaite. “If the hacker succeeds, they take control of your phone number. This way, they can intercept your calls and messages and access services that use your phone number for verification, like two-factor authentication (2FA), potentially allowing them to access your financial accounts.”
Fake eSIM providers
Fraudsters can also claim to be eSIM providers offering end users connectivity services. They will often propose too-good-to-be-true deals that will excite users.
Some of these fraudsters are phishing for sensitive information they can steal while others will collect payments for connectivity services they never intend to offer.
Man-in-the-middle attacks
This is similar to phishing or social engineering attacks in that hackers are trying to gain access to users’ authentication codes. However, man-in-the-middle attacks do not involve impersonation of any kind.
These scammers prey on users who activate or update their eSIM profiles on unsecured networks like public WiFis. Once they gain control of these codes, they can port the eSIM profile to a device they control.
Attack on eSIM management systems
eSIM management systems are platforms in charge of the activation and deactivation of eSIM profiles, remote provisioning, profile management, OTA updates, and the integration of eSIMs with network operators.
Hackers can target these systems and carry out unauthorized activation or deactivation of eSIM profiles, remote control of eSIMs, and manipulation of data across OTA communications.
The vulnerabilities can also come from the network provider. The information of eSIM users can be compromised if network providers are hacked.
There are four other common security risks with eSIMs, according to Utimaco, a cybersecurity company.
Locking profile attacks
Hackers (and unscrupulous network providers) can use a parameter in the eSIM profile to lock it to a specific carrier. When this happens, the user will be unable to switch networks on the device.
A locking profile attack can also make the eSIM unusable.
Memory exhaustion attacks
Attackers can also load excessive data (OTA updates, irrelevant profile data) on an eSIM, leading to memory exhaustion.
When this happens, the eSIIM can malfunction or become unusable. Users cannot activate or deactivate profiles and the ones already created can be compromised, leading to identity theft.
“The goal is for the device to eventually be unable to contact the service provider and will be disconnected from mobile networks,” according to Utimaco.
Undersizing memory attacks
This is an attack that configures the eSIM with insufficient memory, tricking it to assume there is no more memory space.
The lack of sufficient memory will prevent the activation of multiple eSIM profiles and receipt of OTA updates.
Inflated profile attacks
This is a form of memory exhaustion attack. It causes memory exhaustion by adding too many profiles to the eSIM.
3. Securing your customers: How eSIM providers can mitigate security risks
While these eSIM security risks should be a cause of concern, they are not intractable.
eSIM providers, device manufacturers, eSIM resellers, eSIM management systems, and regulatory bodies can all work together to improve the security of this important technology.
What can you do as an eSIM reseller to make eSIMs more secure? Below are some important security protocols to embrace:
Use only reputable carriers
With so many fake eSIM providers tempting users with unbelievable deals, it is your duty as an eSIM reseller to only work with reputable carriers. Before platforming any eSIM provider, you should ensure they are genuine.
This is one advantage of reselling eSIM connectivity services by integrating zendit’s plug-and-play API. We provide you access to more than 80 reputable and trustworthy carriers in over 190 countries.
With us, you don’t ever have to worry about your customers falling victim to fake eSIM providers.
Monitor suspicious activities
If a user is purchasing unusual amounts of data plans or activating an abnormal number of eSIM profiles within a short period, that’s enough ground to suspect foul play.
You can suspend that customer from accessing your website or app while you confirm if they are still the ones in control of their device.
Deploy secure activation channels
We mentioned that eSIMs can be compromised when hackers gain control of eSIM management systems or network providers.
As an eSIM reseller, you are also part of the eSIM management system to some extent. Therefore, you must ensure that your website or app has strong security protocols (data encryption protocols, software updates, web application firewall, secure APIs) that will protect you against hackers.
At zendit, we support you in this by safeguarding you during the API integration process with our top-notch security practices:
- You can regenerate API keys if you believe the former key has been compromised
- Whitelist IP addresses to connect your integration with trusted hosts
- Secure your product catalog by disabling products you don’t intend to sell
- Use ShieldWall to authenticate transactions, and
- Verify the authenticity of any webhook you use in the integration process
Use multiple authentication methods
Two-factor authentication is now a must. Customers want a seamless experience but their cybersecurity makes this extra layer of security essential.
In addition to encouraging your customers to use strong passwords, you can also include biometric verification, codes from authenticator apps, and one-time passwords as additional security protocols.
Have accessible customer service with dedicated lines
When customers can easily reach you when they have been hacked, it will be easier to prevent further losses. Also, having dedicated customer lines that your customers know can make it difficult to impersonate you, thus minimizing the possibility of a social engineering attack.
We exemplify this at zendit. Our customer service agents will support you throughout the integration process and they will be there to answer your questions and resolve any challenges while using our product.
Pay attention to industry standards
As we have seen, GSMA is working hard to ensure there are global security standards to which all stakeholders in the eSIM market must adhere.
Get familiar with these standards and apply the ones that are relevant to you as an eSIM reseller.
Educate your customers
Finally, you should educate your customers about what they can do personally to mitigate eSIM security risks.
Some of the tips you can suggest include:
- Strong passwords: The stronger the password, the harder it will be for scammers to hack it. Encourage your customers to create strong passwords across all important websites and apps.
- Multiple authentication: Even strong passwords are not enough. For important apps, they need to add other methods – biometric verification (fingerprint and facial, available on iPhones and Android phones), one-time passwords, and codes from authenticator apps.
- Software updates: Regularly updating their mobile device’s software is essential. Similarly, they should pay attention to OTA updates and install the latest security patches.
- Avoiding unsolicited messages: Your customers can avoid social engineering attacks if they regularly ignore unsolicited messages from unknown numbers, emails, and social media accounts.
- Avoiding unsecured networks: Man-in-the-middle-attacks rely on the usage of unsecured networks. Encourage your customers to only activate and manage their eSIM profiles on private networks.
- Secure disposal of old devices: Your customers can prevent unauthorized access to their eSIM profiles by deactivating profiles on phones they are no longer using. In addition, they should wipe off all sensitive data before disposing of their phones.
- Cautiously sharing sensitive information: Sharing passwords and other sensitive personal data via chats can be dangerous. Even if their phones are secure, that of the recipient may be compromised.
- Quick response to possible scams: Though the goal is to avoid scams, it’s still important to quickly stop them when they occur. Encourage your customers to report scams and suspicious activities to relevant authorities.
At zendit, we aim to help you set up your eSIM reselling business in the most secure way possible.
You can safely integrate our API into your website and app through our security protocols while gaining access to verified and reputable global carriers that will provide your customers with excellent connectivity services.
By partnering with a security-conscious company like ours, you can set yourself up to offer secure eSIM services to your customers.
Do you want to increase your revenue by securely reselling eSIMs to your customers? Book a demo to see how zendit works or contact us to learn more about how our product can help your business.
Takeaways
- How secure are eSIMs? They are immune to physical theft and cloning and they also support advanced security measures like multi-factor authentication and over-the-air (OTA) updates to patch vulnerabilities.
- While embedded SIMs have enhanced security features, they are still vulnerable to malware, phishing, social engineering attacks, and exploitation of eSIM management systems, among others.
- eSIM resellers can mitigate these eSIM security risks by using only reputable carriers, monitoring suspicious activities, deploying secure activation channels, etc.
- eSIM resellers can also encourage end users to use two-factor authentication, avoid unsolicited messages from unknown numbers, and regularly update their devices, etc.

